Do All Cloud Providers Offer the Same Security Levels?
Cloud computing presents many unique security issues and challenges. Cloud service providers treat cloud security risks as a shared responsibility, whereby the cloud service provider covers security of the cloud itself while customers cover protecting their data from security threats and controlling who has access to it. In fact, most cloud computing security risks are related to data security and are traced back to the data customers put in the cloud.
Public clouds are basically rented cloud computing power or storage and users are just one of many “renters”. With public clouds, all hardware, software, and infrastructure are owned by the provider and storage, hardware, and network devices are shared with other users. Advantages include cost, scalability, reliability, and elimination of cumbersome and expensive maintenance.
Private clouds are used exclusively by one business or government agency. Services and infrastructure are maintained on a private network using dedicated hardware and software. Private clouds provide greater flexibility, high levels of security, and high scalability.
Hybrid clouds are two or more public or private interconnected clouds. In this case, the public cloud is used for high-volume and lower-security requirements and the private cloud for sensitive or business-critical operations. Hybrid clouds provide the most control, flexibility, and the cost effectiveness of paying for extra computing power only when needed.
Companies send their information to a cloud infrastructure that they don’t control and when data is in transit, it’s vulnerable to attack. In public clouds with many users, devices can potentially access this data. Of the many users, research firm ESG estimates that 40% of organizations allow their business partners to access their sensitive cloud-based data, while more than 80% prioritize the security of data on premises verses in the cloud.
There are services that cloud service providers do well:
- They improve the monitoring and tracking of attacks, offering signature and real-time firewall updates, and block unsafe traffic
- They offer 24/7 live tracking and security of websites via support and encryption
- They enhance website speed performance
However, the use of any cloud service comes with the challenges and risks of data security. Various cloud security technologies can be implemented, including:
- Assigning policies to govern what data can be stored in the cloud, quarantine or remove sensitive data found in the cloud, and coach users if they make a mistake and break one of your policies.
- Encryption available within a cloud service protects your data from outside parties, but the cloud service provider has access to your encryption keys. Encrypt your data using your own keys, so you fully control access.
- Limit how data is shared. For example, control information that can be shared externally through shared links.
- Cloud services provide access from anywhere with an internet connection, but access from unmanaged devices like a mobile phone is problematic. Prevent downloads to unmanaged devices through device security verification.
- Apply anti-malware technology to the OS and virtual network to protect your infrastructure.
- The use of third-party tools provides companies with additional security. By using additional encryption, even if a cloud provider gets hacked, the data should remain secure.
In addition to implementing security techniques, there are products that can be added to enhance security. For example, the MikroElectronika MIKROE-2829 - Secure 4 click board features Microchip's ATECC608A CryptoAuthentication technology. It employs an EEPROM array to store up to 16 keys, certificates, consumption logging, security configurations, and other types of secure data. The ATECC608A equipped on the click board supports an I2C interface with a flexible command set for use in various security applications, including Network/IoT Node Endpoint Security, Secure Boot, Small Message Encryption, Key Generation for Software Download, Ecosystem Control, and Anti-Counterfeiting.
 Figure 1: The MIKROE-2829 Secure 4 click board speeds calculations from 10x to 1000x compared to the competition. (Image source: MikroElectronika)
Figure 1: The MIKROE-2829 Secure 4 click board speeds calculations from 10x to 1000x compared to the competition. (Image source: MikroElectronika)
Those asymmetric cryptographic operations are accelerated by the ATECC608A hardware and can be calculated from 10x to 1000x faster than with the software running on standard microprocessors. This prevents the risk of key exposure, which can be found in standard microprocessors. And the device consumes very low current, especially while in sleep mode.
A second board, the Microchip PIC-IoT WG, combines a powerful PIC24FJ128GA705 MCU, an ATECC608A CryptoAuthentication secure element IC, and the fully certified ATWINC1510 Wi-Fi network controller for a simple and effective way to connect an embedded application to the Google Cloud IoT Core.
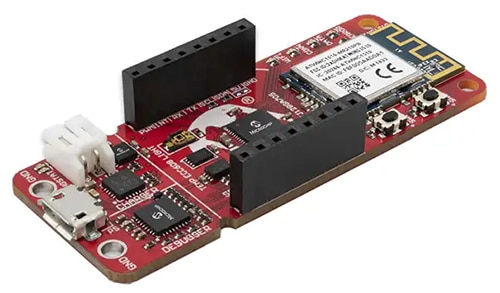 Figure 2: The Microchip PIC-I0T development board provides an easy way to connect embedded applications to the Google Cloud IoT Core.
Figure 2: The Microchip PIC-I0T development board provides an easy way to connect embedded applications to the Google Cloud IoT Core.
The MCU is preloaded with firmware that enables rapid connectivity and sends data to the Google Cloud Platform using the on-board temperature and light sensors. Code is easily generated using the free software libraries in MPLAB Code Configurator (MCC).
In summary, there are many types of cloud service providers. Some, like the Google Cloud, rely on the addition of AI capabilities that will enhance security. All provide infrastructure security. However, the vulnerabilities rest primarily with the users that establish who has control over the data. Cloud computing is not without security challenges that users must mitigate.

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum